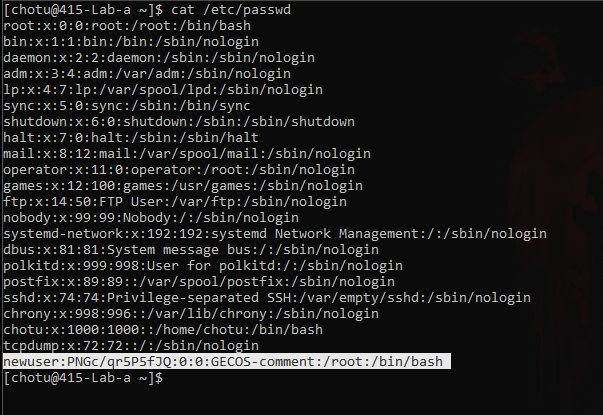
Easy Priviledge Escalation Writeable /etc/passwd – Cyber Security Architect | Red/Blue Teaming | Exploit/Malware Analysis

Linux Kernel 2.6.22 < 3.9 (x86/x64) - 'Dirty COW /proc/self/mem' Race Condition Privilege Escalation (SUID Method) - Linux local Exploit


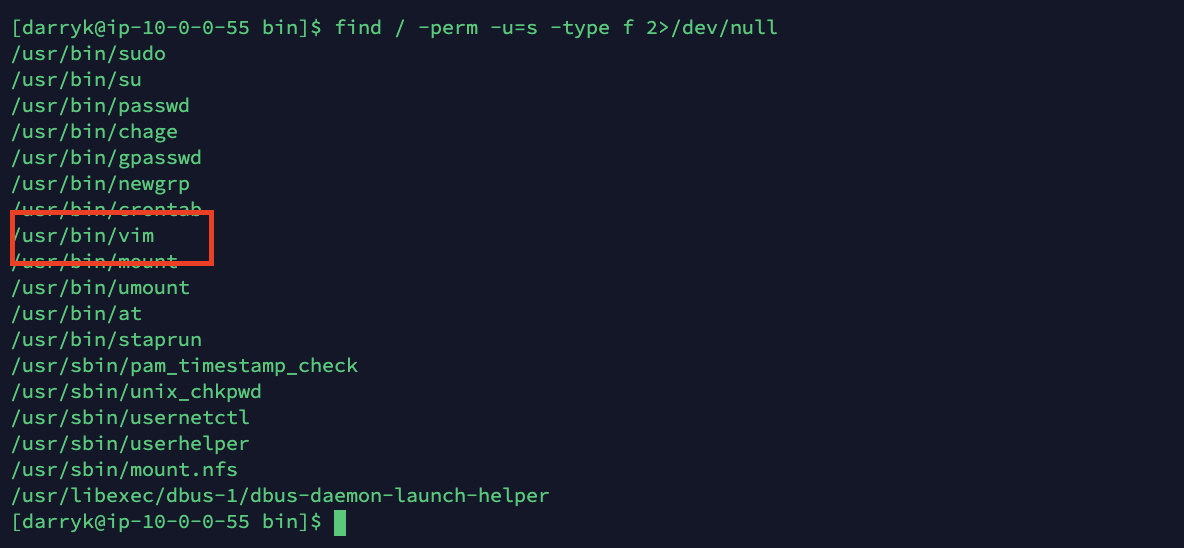







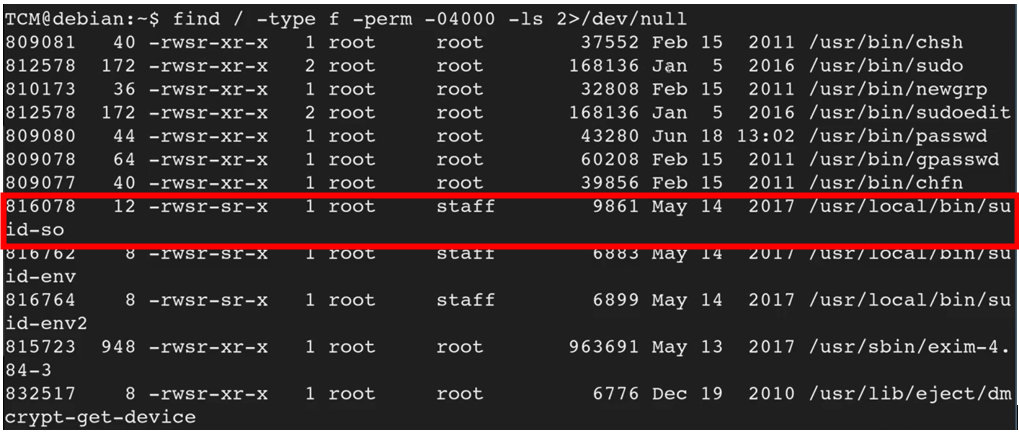
![Linux PrivEsc [TryHackMe] – Revx0r – Security Mindset Blog Linux PrivEsc [TryHackMe] – Revx0r – Security Mindset Blog](https://i0.wp.com/revx0r.com/wp-content/uploads/2021/11/linprivesc.jpg?fit=549%2C212&ssl=1)