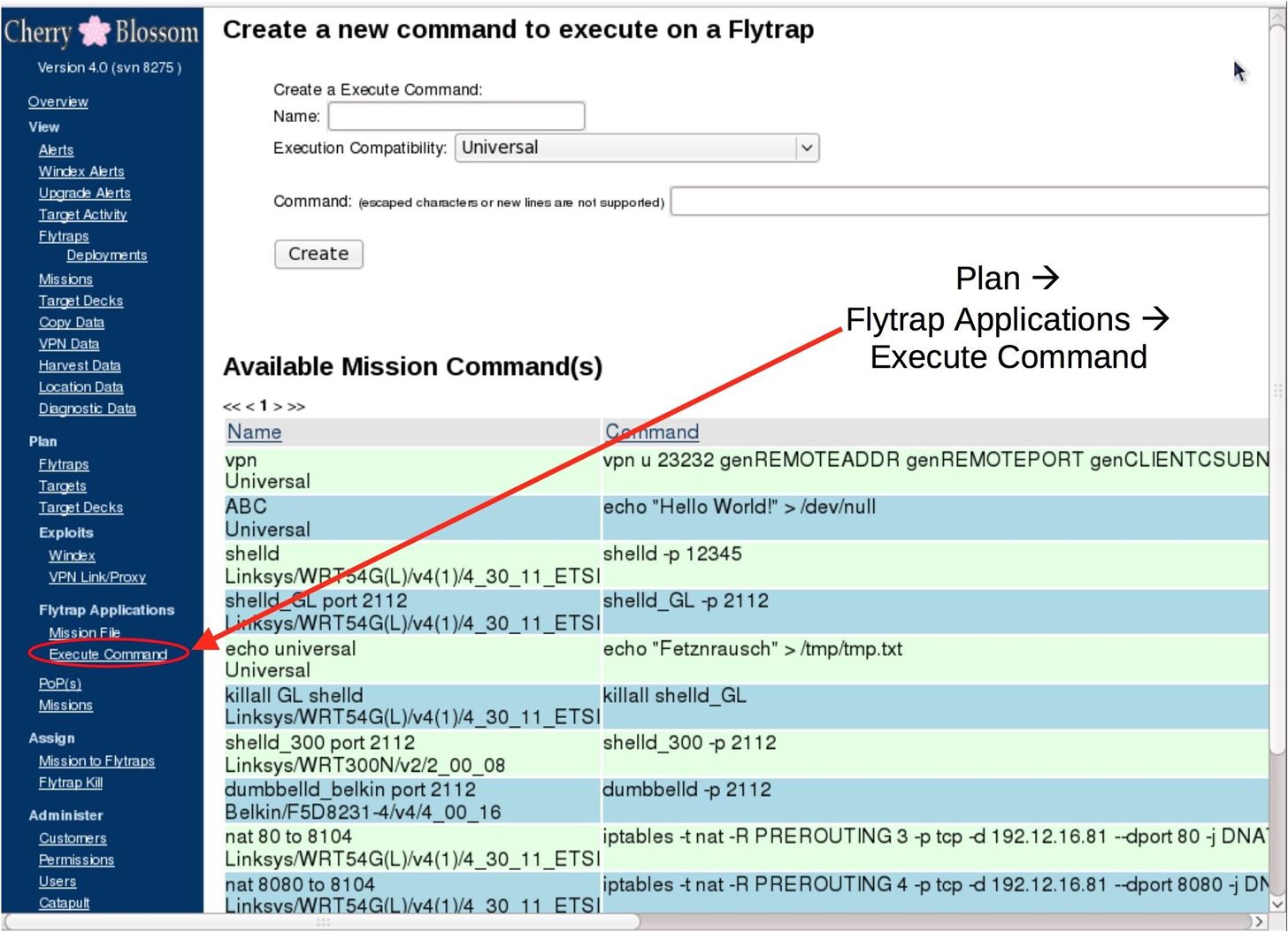
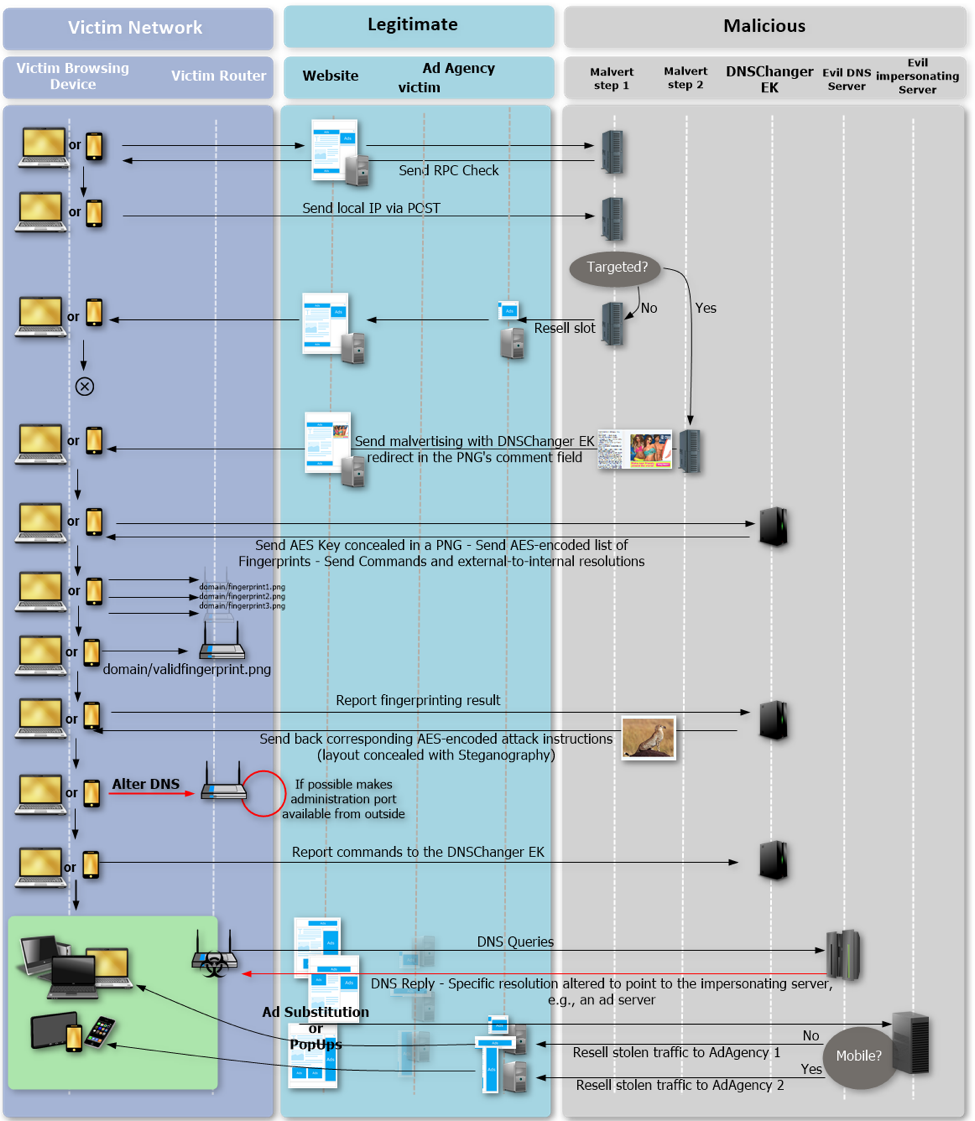
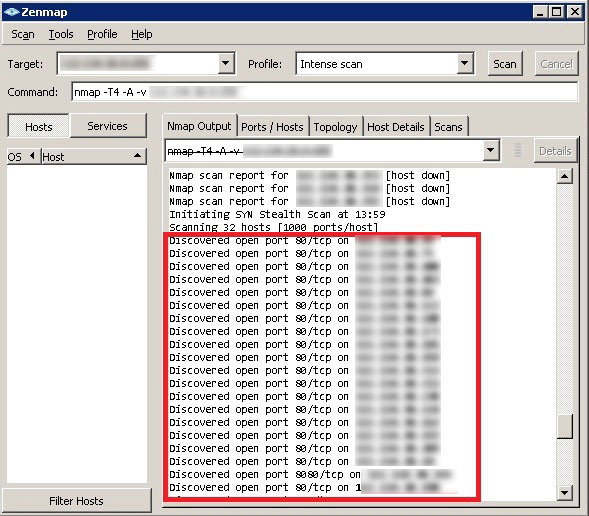
Router Exploit Kits: An overview of RouterCSRF attacks and DNS hijacking in Brazil - Avast Threat Labs

Virus Bulletin on Twitter: "Avast researchers analyse the source code of the GhostDNS router exploit kit https://t.co/5DK3sTDLK3 https://t.co/ENpoVMAyGJ" / Twitter




![Exploit a Router Using RouterSploit [Tutorial] - YouTube Exploit a Router Using RouterSploit [Tutorial] - YouTube](https://i.ytimg.com/vi/u0YrWfze9es/maxresdefault.jpg)