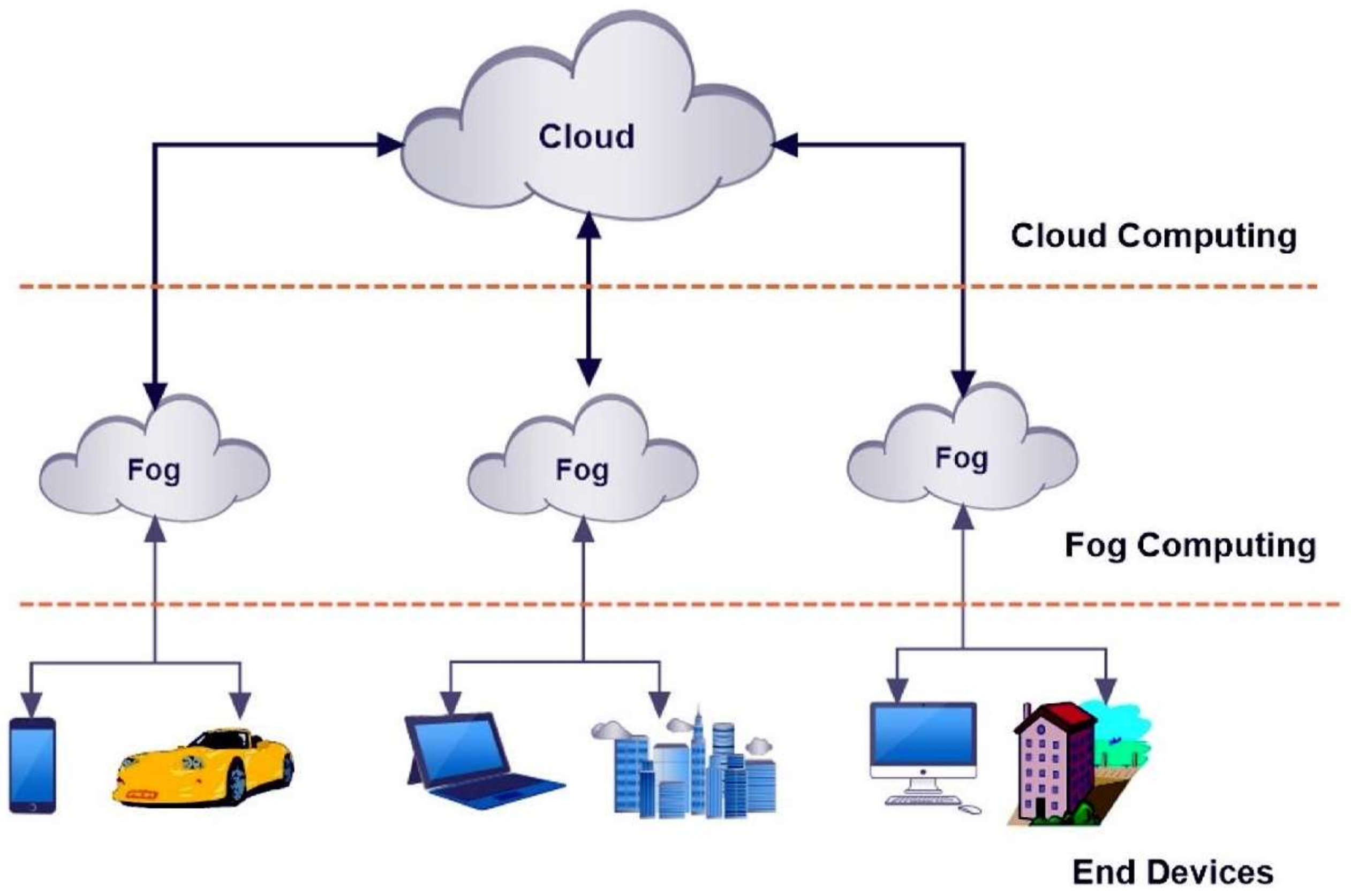
5G-enabled Hierarchical architecture for software-defined intelligent transportation system - ScienceDirect

IoT security vulnerabilities and predictive signal jamming attack analysis in LoRaWAN - Ingham - 2020 - IET Information Security - Wiley Online Library
THC-RPL: A lightweight Trust-enabled routing in RPL-based IoT networks against Sybil attack | PLOS ONE

Large‐scale validation and benchmarking of a network of power‐conservative systems using ETSI's Green Abstraction Layer - Bolla - 2016 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

Migration cost optimization for service provider legacy network migration to software‐defined IPv6 network - Dawadi - 2021 - International Journal of Network Management - Wiley Online Library
![Easy VPN Configuration Guide, Cisco IOS XE Fuji 16.8.x - Easy VPN Server [ Cisco Cloud Services Router 1000V Series] - Cisco Easy VPN Configuration Guide, Cisco IOS XE Fuji 16.8.x - Easy VPN Server [ Cisco Cloud Services Router 1000V Series] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/000001-100000/60001-65000/62001-63000/62829.tif/_jcr_content/renditions/62829.jpg)
Easy VPN Configuration Guide, Cisco IOS XE Fuji 16.8.x - Easy VPN Server [ Cisco Cloud Services Router 1000V Series] - Cisco
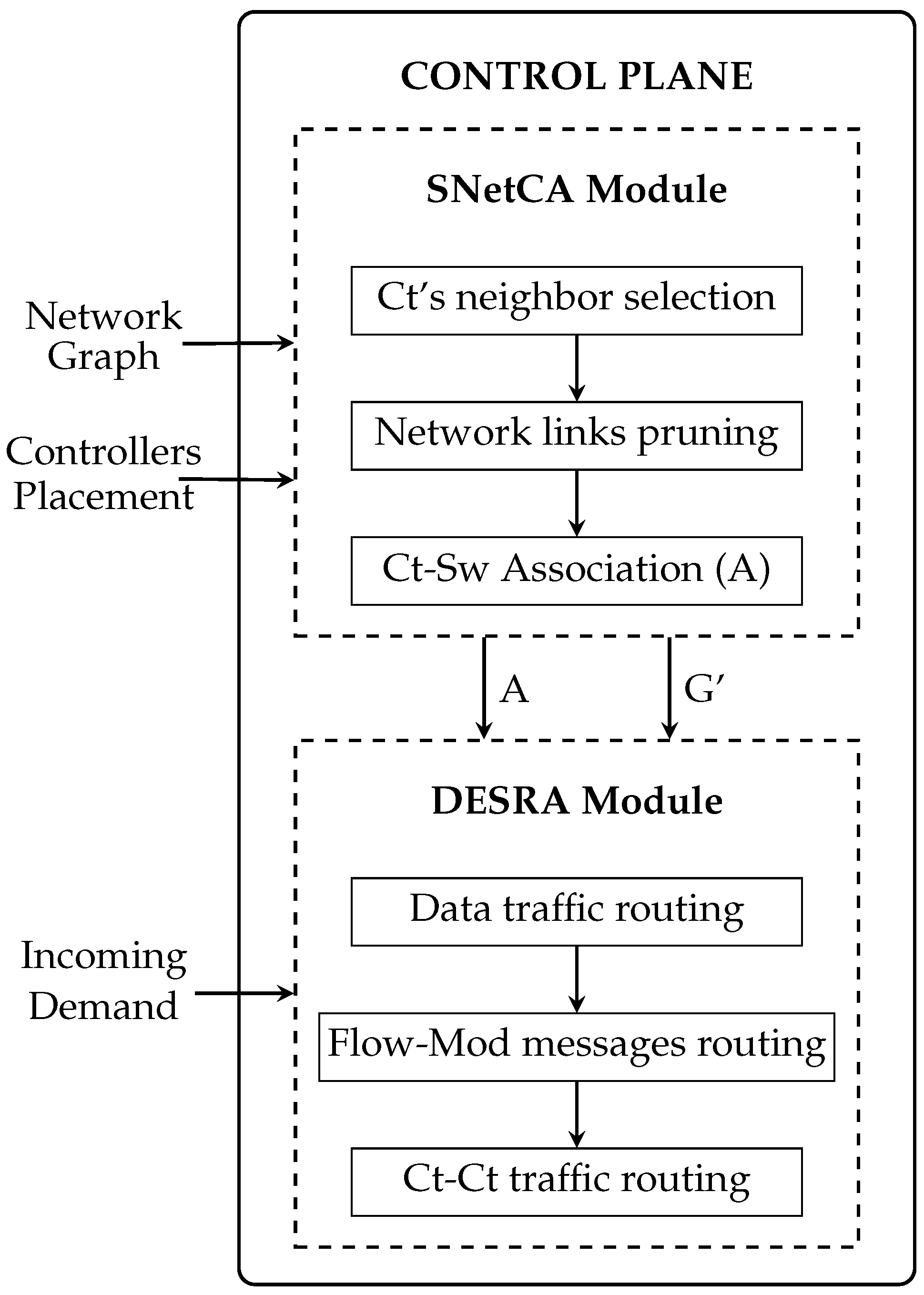
Energies | Free Full-Text | Energy Efficiency and Network Performance: A Reality Check in SDN-Based 5G Systems